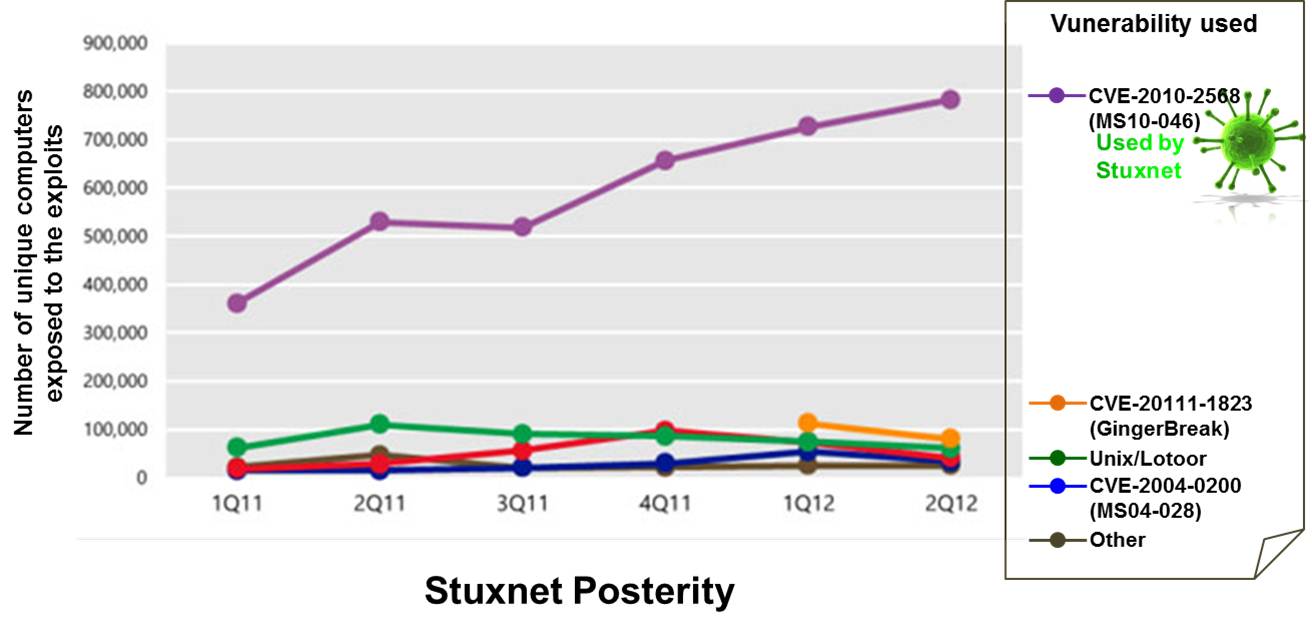
What’s next with Stuxnet?
The history of Stuxnet is now well known even if the country of origin and motivation of the malware developer team has not been officially identified. Stuxnet targets one type of SCADA device, the SCADA system of Iranian Gas Centrifuge Cascade, and it reached its goal.
But has Stuxnet accomplished its fate?
According to the strategic command of the project, the response should be ‘yes’ and it would have been the case if the secret “weapon” was kept secret. In that case, the worm would fall asleep. But, after its discovery by Security researchers, the “too smart” worm still remains awake. Moreover, the Security World gives it a new lease of life. As mentioned on the Microsoft Security Blog by Tim Rains, Director of Trustworthy Computing, and also according to many surveys, the malware seems to open the Pandora’s Box of a new methodology of attacks and will be the common basis for many of them, directly or indirectly (cf. Figure below).
Trust us, there are no more threats!
Even if Microsoft provided a patch for all vulnerable systems, according to independent security specialists: “currently, there are no known workarounds or upgrades to correct this issue” (OSVD review). This is the main reason why there are hacking activities on the same vulnerabilities in 2012. With the deployment of successive patches (and, if the last security patch does not invalidate the former one as sometimes for other manufacturers), thanks to the plentiful literature on this topic to inform users, we can expect that the “beast” will still remain under control. However this optimistic point of view is based on the implementation of good security practices for all potential users (private or organisation) and will be realistic if the management of security, the security awareness, and the incident management capability of every team involved in security increases at the same rate as the threats. The challenge is far from overcome.
Not just a technical problem but a growing-up ethical problem
Moreover, the damage itself still remains: the smart properties of Stuxnet seem to be a very good and huge think-tank for cyber-criminals, and probably thanks to governmental agencies’ efforts funded by the citizens. We could title this unwanted effect “collateral damage” even if, in a traditional war, the collateral damages are usually not funded by the beneficiaries; another good reason to open the discussion without taboo on the status of the cyber-war. Could we consider such a war as “jus ad bellum” (see Stuxnet, Schmitt Analysis, and the Cyber “Use-of-Force” Debate by A n d r e w C . F o l t z) and if yes, should we not try to amend the Geneva Convention as, as software users, we are all concerned?